WHAT IS CMMC 2.0?
The Cybersecurity Maturity Model Certification (CMMC) was introduced by the U.S. Department of Defense (DoD) on January 31, 2020 to ensure the protection of sensitive unclassified information or controlled unclassified information (CUI). Originally, the CMMC framework had five levels of cybersecurity maturity (basic to advanced/progressive) and affected more than 300,000 defense contractors. However, on November 4, 2021, the DoD formally announced the CMMC 2.0 framework. This updated version seeks to simplify the model and reduce compliance costs by streamlining the program and scaling back the requirement that all defense contractors obtain third-party certification of their cybersecurity capabilities. Under CMMC 2.0, about 80,000 contractors will have to undergo third-party assessments while contractors at non-critical CUI levels are able to self-certify. Additionally, contractors who are not yet in full compliance with applicable cybersecurity requirements will be permitted to perform less sensitive contracts if they make a Plan of Action & Milestones (POA&M) and commit to completing the remaining requirements within specified dates. These changes are reflected in the diagram below (published by the DoD):
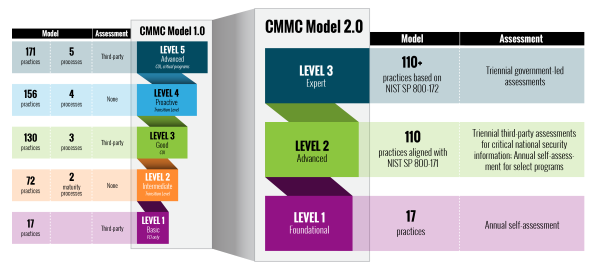
WHAT ARE THE NEW LEVELS?
1️⃣ Level 1 (Foundational) only applies to companies that focus on the protection of federal contact information (FCI). It is comparable to the old CMMC Level 1. Level 1 will be based on the 17 controls found in FAR 52.204-21, Basic Safeguarding of Covered Contractor Information, and focus on the protection of FCI. These controls look to protect covered contractor information systems and limit access to authorized users.
2️⃣ Level 2 (Advanced) is for companies working with controlled unclassified information (CUI). It is comparable to the old CMMC Level 3. CMMC 2.0 Level 2 (Advanced) requirements will mirror NIST SP 800-171 and eliminate all practices and maturity processes that were unique to CMMC. Instead, Level 2 aligns with the 14 families of security requirements and 110 security controls developed by the National Institute of Technology and Standards (NIST) to protect CUI. Accordingly, the 20 requirements in the old CMMC Level 3 that the DoD had imposed were dropped, meaning that the new Level 2 (Advanced) is in complete alignment with NIST SP 800-171. Identified within DoD contracts under DFARS 252.204-7012 clause. DoD is still working to define the “critical” CUI information.
3️⃣ Level 3 (Expert) is focused on reducing the risk from Advanced Persistent Threats (APTs). It is designed for companies working with CUI on the DoD’s highest priority programs, estimated to be about 600 companies. It is comparable to the old CMMC Level 5. The DoD is still determining the specific security requirements for the Level 3 (Expert), but has indicated that its requirements will be based on NIST SP 800-171’s 110 controls plus a subset of NIST SP 800-172 controls.
WHEN WILL CERTIFICATION BE REQUIRED?
The DoD is in the rulemaking process and negotiations with the CMMC Accreditation Body, which is expected to take an additional 9-24 months. While these rulemaking efforts are ongoing, the DoD is suspending mandatory CMMC certification, however, it is strongly recommending defense contractors act now and get CMMC assessed/certified to minimize the risk of DIB companies exposing sensitive unclassified information.
HOW TO GET STARTED
Defense contractors looking to start their CMMC compliance journey should look into meeting the 110 controls in NIST 800-171 as soon as possible, as preparation and implementation can take up to 18 months or more. Not only can we help you achieve NIST-SP 800-171 compliance, but we can also perform a comprehensive gap analysis and determine your current SPRS score. Then work with you on a plan to resolve areas of non-compliance. As a full-service I.T. firm, we can also implement solutions to address gaps so you are ready for CMMC certification and future audits.
CONCLUSION
CMMC 2.0’s cybersecurity standards will better arm the DoD in its efforts to defend against cyberattacks that threaten U.S. critical sectors. But it’s clear that the DoD cannot wait for CMMC 2.0 formalized assessments to improve cybersecurity in the Defense Industrial Base. While the CMMC 2.0 requirements work their way through the federal rulemaking process, enforcement of federal cybersecurity regulations governing defense contractors has stepped up. If you’re seeking future business with the Department of Defense, it’s important you get started on the compliance path right away.
Share this Post

